Tor Fact #1: Tor privately tips off the federal government to security vulnerabilities before alerting the public
This Tor factcheck is part of a series called "The Tor Files: Transparency for the Dark Web," which will use a cache of FOIA documents to explore and expose the close relationship between Tor and the U.S. National Security State. Read more about it here: Fact-checking the Tor Project's government ties. (And get the whole story in Yasha Levine's new book Surveillance Valley: The Secret Military History of the Internet.)
Note: This is the first in what will be a series of "Tor fact-checks"...check back for more!
CLAIM #1: Tor does not provide backdoors to the U.S. government
RATING: Moderately true.
While the documents do not show Tor employees providing backdoors into their software, they do reveal that they have no qualms with privately tipping off the federal government to security vulnerabilities before alerting the public, a move that would give the feds an opportunity to exploit the security weakness long before informing Tor users.

Take the incident involving "TLS normalization."
In 2007, Tor developer Steven Murdoch wrote up a report on the problems and vulnerabilities connected to the way Tor encrypted its internet connection. Turned out that it did so in a very unique way, which made Tor traffic stand out from all the rest and made it easy to fingerprint and single out people who were using Tor from the background data noise of the internet. Not only did this encryption quirk make it easy for foreign countries to block Tor (at the time Tor's efforts were targeted primarily at China and Iran), but in theory it made it much easier for anyone interested in spying on and cracking Tor traffic — whether the NSA, FBI or GCHQ — to identify and isolate their target.
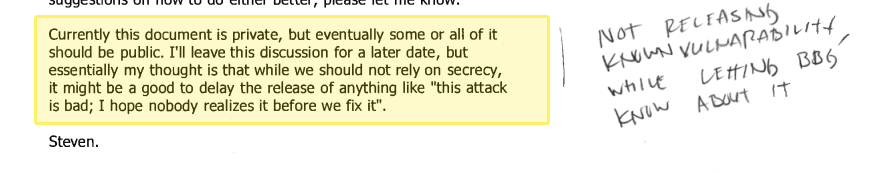
In his email to Tor cofounder Roger Dingledine, Murdoch suggested they keep this vulnerability hidden from the public because disclosing it without first finding a solution would make it easy for an attacker to exploit the weakness: "it might be a good to delay the release of anything like 'this attack is bad; I hope nobody realizes it before we fix it'," he wrote.
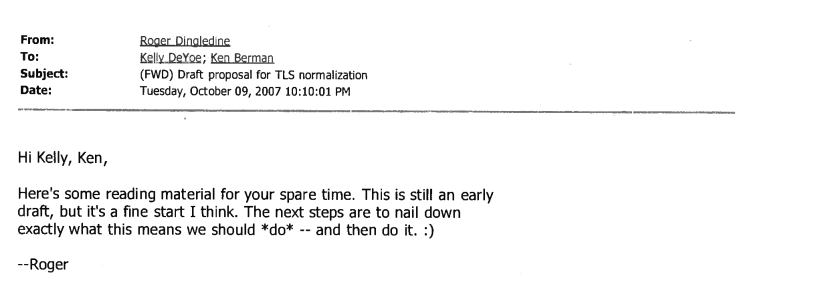
Dingledine agreed. He didn't tell the public. But he also didn't keep the information private. He did something very much the opposite: he debriefed his backers at the BBG, an agency that had been spun off from the CIA and continues to be involved in covert change efforts around the world. (For my reporting on this history see: Surveillance Valley.) Roger forwarded his exchange with Steven to the BBG, making it clear that they would not be fixing this vulnerability anytime soon and that the public would be kept in the dark about this fact. He ended his email with ":)" — a smiley face.
How cute.
Privately tipping off a spooky federal agency deeply embedded in the U.S. National Security State to a vulnerability? No matter how slight the weakness being reported, you'd have to be naive to think that the U.S. government would not move to exploit it.
Don't know about you, but I'd wager most Tor users wouldn't be too happy knowing that this goes on at Tor. I'd wager they'd see it as nothing less than a total betrayal of trust. A double-cross. To them, Tor is not supposed to be giving advance warning to the U.S. government about it's vulnerabilities. It's supposed to be fighting on the other side: a rebel grassroots privacy tech outfit building tools that thwart the most powerful governments and intel agencies in the world. That's the mystique and that's the promise. That's supposedly why Tor's endorsed by the EFF and Edward Snowden, the most celebrated government whistleblower in recent memory. Some, like Ross Ulbricht, proprietor of the original Silk Road, staked their lives on their belief in Tor's independence and anti-state nature. Maybe it's not a surprise that Ulbricht is now spending life behind bars.
This brief interaction (and there are many many others on all sorts of topics) gives you a glimpse into the kind of friendly backroom relationship Tor has with the U.S. government. Fact is, Tor does not see the BBG as a threat. How can it see it that way? The BBG is a major benefactor, handing out over $6 million in contracts to the Tor Project from 2007 through 2015. The BBG is a friend and source of funds — and Tor management is eager to please. And of course the BBG isn't Tor's only friend in the U.S. government: the U.S. Navy and the State Department have also funneled millions into the project, and continue to do so today.
So...How long did it take for Tor to reveal this security weakness to the general public?
Well, it's hard to say. But looking through Tor's "tor-dev" mailing list it appears the document Roger initially shared with the BBG in 2007 was brought to the public's attention only in 2011. That's four years after the federal government was tipped off about it!
Note: The thing to remember is that Tor's BBG correspondence only reveals a sliver of Tor's full interaction with the feds. Much of the funding for Internet Freedom tech takes place under Radio Free Asia's umbrella, a private government corporation that claims it does not fall under FOIA mandate and so refuses to comply with journalists' FOIA requests. We also do not know what Tor reveals to its other two backers, the State Department and the U.S. Navy. Nor do we know what Roger Dingledine or other Tor managers reveal in their regular meetings with U.S. intelligence and law enforcement agencies. And there are many such meetings.